 One of my personal goals is to teach myself how to program in java. After falling asleep while reading tutorials, I clicked on youtube and then found Bucky Robert’s java tutorials. They are good. After going through the first 18, I clicked on his website thenewboston.org, and read this on the ‘about’ page:
One of my personal goals is to teach myself how to program in java. After falling asleep while reading tutorials, I clicked on youtube and then found Bucky Robert’s java tutorials. They are good. After going through the first 18, I clicked on his website thenewboston.org, and read this on the ‘about’ page:
I soon realized that these videos were something more than just another cat video on YouTube. They were a gateway to a higher education, for free. While Universities and Corporations were charging like crazy for people to receive an education, people could come and watch my videos and get the same information for no cost at all. I decided that this is the way it would be. An education should be free for everyone who desires one. It should not be a business. And quickly, that became my goal.
So, while most assholes who declare ‘education should be free’ really mean someone else should pay for a the bloated over-priced scam that is the state-run higher education system, this guy is actually doing it. He is educating people for free, at his own expense! Based on his youtube channel‘s stats, I’d say he is doing a great job of it too!
Hats off and many thanks to Bucky. This type of action is the future. Individuals providing, for free or near-free, what huge organizations provide for huge piles of money. Doing it better, more efficiently, and more effectively. Here is my favorite part: He is doing it because he thinks it is the right thing to do, and (hopefully) he is making a living teaching what he loves to others. By the way, rah rah free Internet (as in freedom). Let’s keep it that way!

Like this:
Like Loading...

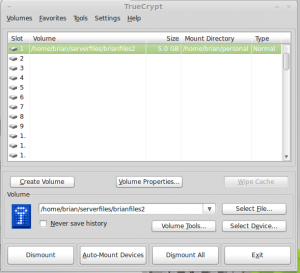 I recently converted some of my personal folders (like MyDocuments) to reside within an encrypted file. Besides the obvious benefit of keeping the information in that folder more private, another reason was so I can take the contents of the folders with me anywhere (on a external USB drive) and not have to worry about what would happen if I lost the drive or what other people would see if they borrow the drive. (In the un-encrypted state, the folder looks like a big file on the drive full of gobbledgook) Another advantage is that if the drive is stolen, they won’t have all my personal documents, they would just have some encrypted files that are meaningless. Since the whole folder is housed within one file, copying, syncing, and backups are easy too.
I recently converted some of my personal folders (like MyDocuments) to reside within an encrypted file. Besides the obvious benefit of keeping the information in that folder more private, another reason was so I can take the contents of the folders with me anywhere (on a external USB drive) and not have to worry about what would happen if I lost the drive or what other people would see if they borrow the drive. (In the un-encrypted state, the folder looks like a big file on the drive full of gobbledgook) Another advantage is that if the drive is stolen, they won’t have all my personal documents, they would just have some encrypted files that are meaningless. Since the whole folder is housed within one file, copying, syncing, and backups are easy too.
 One of my personal goals is to teach myself how to program in
One of my personal goals is to teach myself how to program in 











